Personal VPNs Can Be Shady, but Should Companies Ban Them?
It sounds like a psychological experiment.
Give an animal a treat whenever it wants, instantly, for performing a simple trick. Teach it to expect that, and it will likely become docile, happy to comply under the terms of the arrangement. Then, gradually, increase the difficulty of the trick. Or have it perform the trick, but receive no treat. Or show it a big pile of treats that it is forbidden to eat. How long before it stops performing? How long before it makes a mad dash for the forbidden treats? How long before it bites the researcher?
If you’re an American internet user in 2024, you are essentially the subject of this experiment. You were trained to expect digital services that were cheap and easy, but lately they have become expensive, invasive, or simply impossible.
Streaming prices keep increasing while streaming content keeps disappearing, news stories are aggressively paywalled, and seven states (so far) have passed laws requiring pornographic websites to verify the age of their users, often by sharing their driver’s licenses.
These changes are driving users onto the gray market of VPNs, which promise a private, secure browsing experience that lets them get around these restrictions. The problem is, VPNs are often neither private nor secure. The VPN industry is riddled with scandal and intrigue, and it’s difficult (by design) for the average user to tell responsible vendors from bad operators.
Naturally, individual users should be aware of the security risks of VPNs (and if that describes you, keep reading), but security and IT professionals have cause for concern as well. When employees use VPNs on the same devices they use for work, they open the door to all kinds of security issues.
So let’s talk about why people are flocking to personal VPNs, why they can be so risky, and how companies can provide sensible education and policies around their use.
Personal vs Corporate VPNs
Before we go any further, it’s important to distinguish between the two types of VPNs. Many companies use corporate or enterprise VPNs so their employees can securely access their private corporate networks. These VPNs have some issues of their own, but they are by and large established solutions run by reputable companies.
Both corporate and personal VPNs use the same “tunneling protocol,” which hides an individual’s IP address and encrypts their data. But personal VPNs do so with the express goal of anonymous internet usage, and are often less secure and trustworthy.
Why People Use VPNs
If you’re concerned about your co-workers endangering security through VPNs, it’s not enough to simply issue a blanket ban on them. For one thing, anyone using a private VPN has already shown that they’re willing to go around rules they don’t agree with. For another, you likely lack the ability to enforce such a ban on any devices not managed via MDM.
Instead, you must start by reckoning with why and how workers are using VPNs. Then you can educate them on the risks and design thoughtful and effective policies.
Content piracy
In the past few years, streamers like Netflix and Amazon Prime have steadily increased their prices, cracked down on password sharing, and introduced ads. They’ve removed and georestricted content–either as part of Byzantine licensing agreements or to cut costs. As a result, they’ve driven people back to media piracy and torrenting sites.

When you arrive on a torrenting or piracy site, one of the first things you’ll see is an advertisement for VPNs. A study from the Digital Citizens Alliance and White Bullet estimated that VPN services spend $45 million per year advertising on these sites. (These sites pose their own security risks, and the report points out that “the links between piracy, malware, and credit card fraud have been well documented.”)
Some VPN users also value the technology’s ability to skirt paywalls on news sites, since if your IP address is constantly changing, you’ll never hit the dreaded “five article limit.” It may not be piracy in the traditional sense, but at least now the newspapers know who to blame for the death of journalism.
So, is content piracy a “valid” use for VPNs? That’s a thorny question, but it’s at least easy to see their appeal in this scenario; a VPN will mask your IT address so you don’t have to worry about the FBI banging down your door just because you wanted to watch Andor.
Bypassing geo-blocking
The United States isn’t among the biggest VPN markets (we’re 12th at last count); first place belongs to the UAE, followed by Qatar, Singapore, and Saudi Arabia. As you might notice, these are countries that heavily restrict internet usage and police online speech. In such countries, using a VPN is a matter of safety, especially for journalists, dissidents, or anyone whose work or personal life could make them a target of surveillance. Of course, VPN usage itself also poses risks in many of these countries; VPNs are banned or highly restricted in China, Russia, and the UAE, among others.
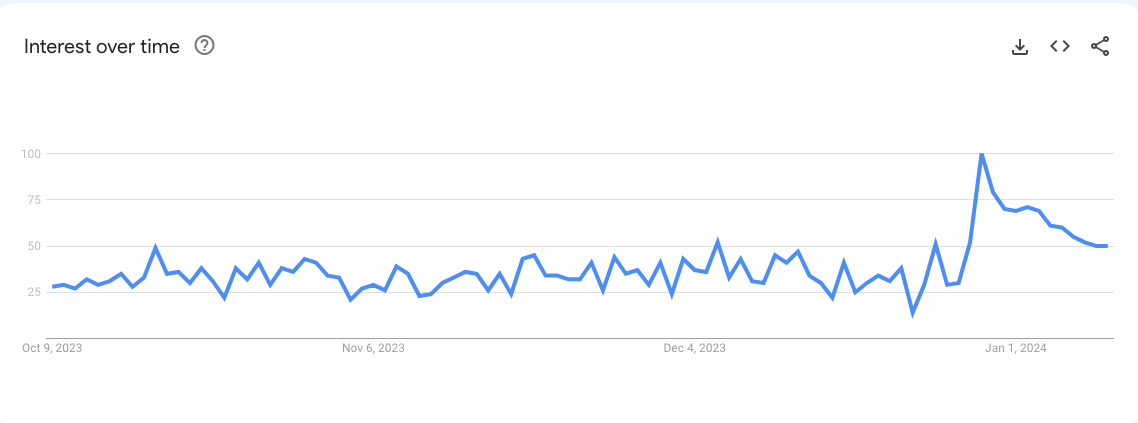
In the United States, recent age verification laws on porn sites show exactly how geographic restrictions drive people to use VPNs. When Virginia enacted its law in July 2023, it quickly came to lead the nation in Google searches for “VPN.” The same thing happened in North Carolina when it enacted its own law a few months later, as this Google Trends graph shows.
But using a VPN to get around geographic restrictions doesn’t have to be a high-stakes game of politics and freedom; plenty of Western users like to watch Canadian Netflix or UK TV. And if you Google either of those terms, guess what you’ll find. That’s right, advice on getting a VPN.
Security on public wifi
This was one of the original use cases for corporate VPNs. Before https became standardized across the internet, anyone at a Starbucks could peek at your browsing. These days, public wifi is safer than it used to be, but still not entirely free from man-in-the-middle-attacks and intrusive data collection. VPNs can be a sensible solution if you have to transmit sensitive information while on a public network.
Evading “personalized pricing”
This might be the most niche use case for VPNs, but it’s interesting enough to warrant a mention.
Companies that use personalized pricing adjust their costs based on whatever data they can collect on a consumer. As one vendor excitedly explains, “Hyper personalization works more effectively than other pricing strategies as it is based on key user features, such as their willingness to pay — the maximum price users are willing to pay for a product.”
Many companies deny using dynamic pricing, but many users report that they can get better deals by using an IP address that isn’t associated with their identity, and that places them in a less affluent area code. So if you do have a VPN, be sure to test that theory the next time you’re booking plane tickets.
Risks of Personal VPNs
VPNs present a number of security and privacy risks, and the VPN market is plagued by unscrupulous (or at least suspicious) companies. Not every VPN company is shady, of course, but there’s no easy way to tell the good from the bad; perhaps the most dangerous aspect of VPNs is how difficult it is to figure out who to trust.
VPNs are extremely dangerous if compromised
By their nature, VPNs are designed to bypass security measures like firewalls and proxy servers, so users can access the content they want. But this feature becomes a massive bug if something goes wrong.
Unit 42’s report on VPNs lays out one risk, in which VPNs bypass proxy servers:
“…proxy servers protect corporate endpoints from communication with malicious command and control (C2) servers. However, through VPNs, users can bypass this protection. For example, if an employee’s computer gets infected while using a VPN, the data sent to the C2 server will not be visible to the InfoSec team.”
VPNs are also vulnerable to exploitation by bad actors if not kept properly patched. The same Unit 42 report includes a table of popular VPNs and their known vulnerabilities, many of which give hackers the ability to escalate their privileges and remotely execute commands.
VPNs can log, store, and sell user data
VPNs work by creating a secure tunnel, through which no one, not even your internet service provider (ISP), can see your browsing behavior. Well, no one can see it except the VPN itself, and the VPN can see everything. You have to put a lot of trust in a VPN to use that power responsibly, and they have not always earned that trust.
“We typically engage a VPN service to better protect our online privacy, while understanding that all of our data – every click, every site, every background app – is being funneled to a single company, whose servers most of us will never see with our own eyes.”
-Rae Hodge, CNET
The data VPNs can access has value to advertisers, among others, and with that value comes the potential for misuse. As Unit 42 points out, “VPN providers could double-dip users and businesses by taking subscription money from users and selling users’ web consumption data to the advertising industry. In more extreme cases, they might even supply user data to government authorities.”
The best way to avoid this risk is to use a no-log VPN, which doesn’t store this data. But you can’t always trust VPNs to tell the truth about their logging policies.
VPNs have been caught lying
In 2020, over 1TB of user data from tens of millions of customers–including plaintext passwords and browser histories–was found unencrypted on a cloud server. The shocking thing? This data came from seven VPN companies, all of which claimed to have “no logging” policies.
In 2023, Australia’s Federal Court ordered two Facebook subsidiaries–Facebook Israel and Onavo Protect VPN–to pay a $20 million fine for secretly recording user activity on a free VPN and sharing the data with Meta. IT News Australia reported that: “The VPN was promoted on platforms like Google and Apple App Store as a way to ‘protect personal information’ and to ‘keep you and your data safe’.”
There are plenty more stories like this, but in the interest of time, we’ll just share one more egregious example. In 2015, cybersecurity researchers exposed Hola, a free VPN that turned out not to be a VPN at all. Instead, Hola was a peer-to-peer network that let anyone else using the network see your activity, not to mention install malware on your device. What’s worse is that Hola was working with a company called Luminati, which used Hola-connected machines to run massive botnet operations without user knowledge.
The most shocking part of this decade-old story is that Hola is still around! It’s got a 4.6 rating on the Google Play store and no mention of this scandal on its Wikipedia page. (Luminati is still kicking too, though today it’s called “Bright Data” and has been involved in multiple other scandals.)
The fact that users can ignorantly download VPNs with such checkered histories isn’t an accident. It’s because VPN providers spend a lot of effort laundering their reputations and then hiding their footprints.
VPN companies own their competition…and their critics
For the past few years, VPN companies have ridden the same wave of M&A deals as the rest of the tech industry. In 2022, CNET reported that three companies own many of the most popular VPNs on the market, creating the illusion of competition and choice.
The big players are Nord Security, which owns NordVPN, Atlas VPN, and Surfshark; Ziff Davis, which owns IPVanish and StrongVPN; and Kape Technologies (formerly Crossrider), which owns CyberGhost VPN, ZenMate VPN, Private INternet Access, and ExpressVPN.
The often-confusing ownership structure of these companies makes it even tougher to understand their policies. CNET’s Rae Hodges wrote a 2020 deep dive in which she tried to determine whether CyberGhost’s data policies remained the same after their acquisition.
In the end, she concluded that: “…although CyberGhost’s business jurisdiction is in Romania, CyberGhost could share your data with not only its UK-based parent company, but with its US-based sibling company.”
Several VPN companies also own VPN review sites, along with other tech media properties. Ziff Davis owns Mashable, PCMag, and Encrypt.me, among others. Kape Technologies owns vpnMentor and WizCase. Some sites are more or less open about these relationships, and all claim to be editorially independent, but you’re still unlikely to see any of them attack their parent companies. Also, you can assume that the examples above are just the tip of the iceberg.
If you click on a “best VPN” listicle at random, you might notice something fishy. That’s what I did, and I found a polished-looking website that seems to employ a real team of writers, even if they do acknowledge that they “may earn compensation” from some of the companies they review. But who owns the website? A “media” company whose own website shows that they create independent-looking “review sites” across numerous industries to help their customers make more sales.
This isn’t to suggest that every person reviewing VPNs is an industry plant–but these murky relationships create an atmosphere of suspicion, even as VPNs ask for our trust.
How To Protect Company Data From Employee VPNs
If you work in security or IT, you might feel a little torn when it comes to VPNs. Maybe you use a VPN in your personal life, but don’t want them anywhere near your company’s end users and their devices.
So what are your options?
Well, if you work for an in-person company, you can block most personal VPNs on your office network by blocking commonly used ports like UDP port 500. And it’ll be pretty obvious if someone is using a VPN on a local wifi network since their traffic will appear geographically impossible.
But it gets trickier once you start thinking about employees working from home and on their personal devices and networks.
If you only allow managed devices to access company resources, blocking VPNs shouldn’t be a challenge–you can prohibit such downloads via MDM, by maintaining a blocklist of untrusted VPNs (although this requires significant maintenance) or by prohibiting VPNs altogether (although this would stop them from using a corporate VPN if they had one). But, as Kolide’s own research has shown, nearly half of companies allow unmanaged devices to access their resources. Your options for blocking (or even knowing about) VPNs on those devices are more limited.
When we’re talking about blocking applications on an employee’s personal device, the issues are ethical as much as technical. Is it fair to ban all personal VPNs on employee-owned devices, even knowing that they can be a vital tool for protecting privacy? Is it enough to simply ban the worst offenders and do your best to ensure that more trustworthy VPNs stay updated? There aren’t universal answers to those questions, but there is some advice that should apply to most companies.
Educate users
Most users don’t go looking for VPNs–they stumble on them in the course of trying to watch a show, get around a paywall, etc.. And so most users have no idea that they should be very careful about what provider they pick and how they use it.
So, the first step in improving safety is to educate users on the risks.
Unfortunately, you can’t just send out a memo telling users to be cautious when picking a VPN, not when there’s so much bad information floating around that makes it so difficult to make a good decision. Figuring out where a VPN stores data or assessing its log policy is already more work than the average user is equipped to do. And even if they do it, these companies have been caught lying about precisely these policies!
The safer route (if you choose to allow/accept VPNs at all) is for someone with a technical/security background to come up with a list of trustworthy VPN providers, as well as vendors to avoid. Likewise, you should discourage or ban the use of “free” VPNs–these days, everyone should know that if a product is free, it means you’re the product.
Enforce VPN policy even on unmanaged devices
IT and security teams are well within their rights to ensure that no device that touches company data is susceptible to malware or data leakage via an MDM.
There are two general ways to accomplish this:
Prevent unmanaged personal devices from accessing company data.
Ensure that personal devices meet security requirements and aren’t using unauthorized VPNs.
In either case, a device trust solution is the most reliable way to accomplish your goals for devices outside the scope of MDM. (Device trust isn’t the only way; you can also try to sandbox work resources via VDI or corporate VPNs, but then you’re still running the risk of a malware-infected device sneaking past those defenses, for example, via a keylogger.) Any device trust solution ensures that no device can authenticate unless the device trust agent is present–so you automatically block all unknown devices.
You can also go further with Kolide’s device trust solution, which allows you to write custom checks and define your VPN policy as you see fit. Kolide admins can use our custom check editor to ban all third-party VPNs, allow only trusted VPNs, require VPNs to be patched regularly, or ensure that a personal VPN is turned off while the user is working.
Crucially, Kolide doesn’t enforce these policies through brute force (like MDM); it notifies end users directly so they can take action themselves, as well as explaining the reasoning behind the policy.
The beauty of this user-driven approach is that it doesn’t use the same arbitrary, invasive tactics that drove people to VPN in the first place; it’s clear and considerate.
Workers and Businesses Need VPNs They Can Trust
When Obi-Wan and Luke are looking for a ride off of Tatooine, they don’t go to the shiny, Empire-sanctioned spaceport. They’d never make it off the ground! They go Mos Eisley, where they can find a captain willing to bend the rules.

It’s much the same with VPNs; they have to exist in an ethically gray area in order to function at all. And there are a lot of people who absolutely rely on VPNs to function, especially in states or countries clamping down on internet freedom.
But gray areas also leave a lot of room for bad actors to operate, and that’s where responsible IT and security teams come in.
Want more original and curated stories about IT and security? Subscribe to the Kolide newsletter.