Better Together: New 1Password Checks
Happy BlackHat Everyone! Even though I’m writing this from the sweltering desert of Las Vegas, Nevada, I couldn’t feel any cooler than I do right now as I discuss some new Kolide Checks we’ve released as a companion to all the exciting announcements we made at 1Password. If you haven’t read them yet, what are you waiting for? Pocket Aces? Head over to the 1Password blog and check them out!
The theme of these Checks is “better together,” in that they both demonstrate how the capabilities of Device Trust and 1Password can join forces and make something far greater than the sum of their parts.
Check #1: Require 1Password be Logged into Work Account
1Password is a tool you buy for your users to make sure that when it comes to credentials like passwords, SSH keys, passkeys, and other sensitive data, the right and secure way becomes the easy way!
Unfortunately, 1Password can’t help you or your users if it’s not installed on their computer. Sometimes, though, the problems are more nuanced. What if it’s installed, but it’s an old version? What if it’s installed but the user is only saving passwords in their personal vault? What if they’ve installed the desktop app but not the browser extension?
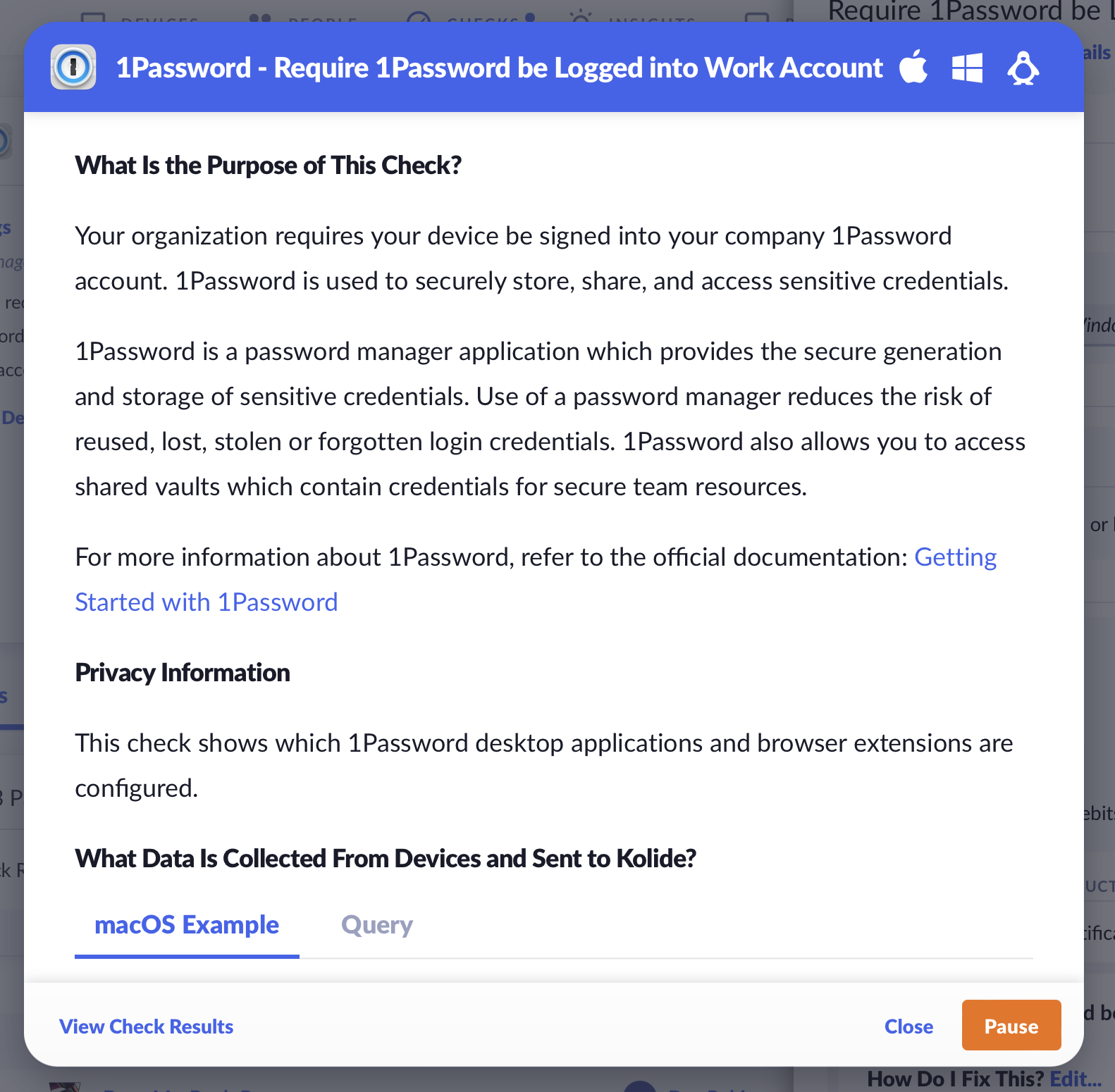
With this new Check, we can help. Our new Check ensures that the following are true:
- That a modern version of 1Password is installed on their computer
- That it’s running in the user’s web browser (optional)
- That it’s configured to point to one of your preferred 1Password accounts.
Even better, this Check works across macOS, Windows, and Linux and is compatible with all major browser vendors that 1Password’s extensions support. How cool is that?
If a user fails this Check and you turn on end-user remediation, they will be given step-by-step instructions to get 1Password installed. As with all of our Checks, you can customize these instructions to best suit your needs.
To configure this Check simply:
- Enable it in the Check Catalog
- In the edit sidebar, scroll down to Options and click Configure
- Add at least one allowed 1Password Sign In Address (e.g.,
michaelscottpapercompany.1password.com) to the configured options and click Save. - That’s it!
Once you get a feel for this Check, our recommendation is to turn on a end-user remediation strategy, so you can make sure your end-users are using 1Password correctly.
Check #2: Require SSH Keys to be Encrypted
While we showed in the previous section how Device Trust can help you roll out 1Password, this section describes how using 1Password can actually make end-user remediation even easier!
Since we launched, Kolide has had a Check to make sure developers are encrypting their SSH keys. Unfortunately, the end-user fix instructions for this Check require that a developer open the terminal, run a command, and then set a passphrase.
While this gets the job done, it’s not ideal. What happens if the passphrase isn’t complex? What if the developer loses the passphrase?
1Password’s desktop app actually makes it really easy to secure SSH keys by enabling you to import them directly into the solution and they also have an SSH agent to make it simple to discover and leverage these credentials automatically when you sign into a server.
To take advantage of these capabilities, we’ve updated our Require SSH Keys to Be Encrypted Check, to offer the ability to launch 1Password and begin the process of importing the key with a single click.
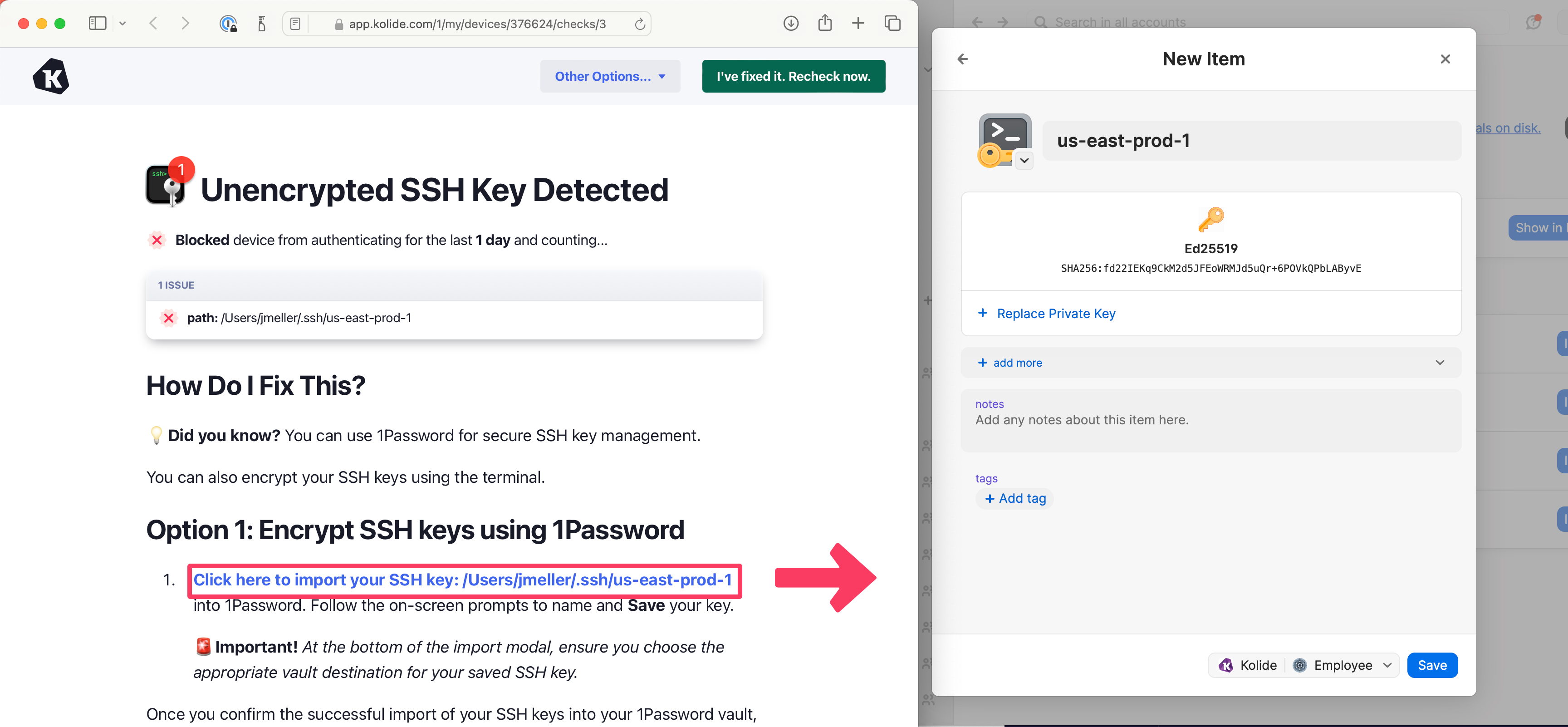
If the device doesn’t have 1Password, we intelligently re-order the fix options so that our previous method is listed right at the top.
As you can see, when 1Password and Device Trust work together through Extended Access Management, you can do a lot more! We plan on iterating on these features and introducing more this year. If you have thoughts, let us know!





