All the Highlights From Oktane 2023
In 2023, there are two things that are guaranteed to grab headlines: Taylor Swift and AI. And for this year’s Oktane, that marketing playbook was on full display. While I’m ambivalent towards Swift’s music (it’s fine), I was impressed by a keynote that put attendees on a journey to buy “Tailor Swift” tickets while dodging malware and using Okta’s new AI products.
In the pop star-inspired session, we saw Universal Logout, Log Investigator, and Policy Recommender—all with “Okta AI” at the end of their product names—in action. We’ll get into each of these features below, but the sheer number of AI products Okta announced (double digits!) tells you a lot about the message of Oktane 2023.
Before we get into the new features, we’ll add the same safe harbor disclosure that Okta had at the beginning of each session. Basically, everything we learned about upcoming product changes are “forward-looking statements.” That means that release timelines and the features themselves are subject to change so you shouldn’t make a buying decision based on what you learn (although we can’t stop you from being excited).
While my Kolide colleagues at Oktane spent most of their time at our wonderful booth (a cozy fire for spooky season), I bounced from keynote to keynote and session to session. All of the Oktane sessions are available to watch, so you can follow along on your own as we dive into what I learned and took away from Oktane 2023.
Okta Goes Beyond
At a tech conference, like a kid’s birthday party, everything that isn’t nailed down must be on theme. In this case, Okta’s theme was “go beyond,” and that phrase was featured in the title of many keynotes and sessions.
One of the areas where they plan to go beyond is device trust (and as a device trust company, we have to talk about this first). Delivering on their oft-referenced promise of extensible neutrality (fancy speak for being open to new systems and vendors), Okta is now allowing customers to integrate device posture checks of their own and from third-party vendors—which yes, includes us!
This doesn’t replace Okta’s existing device trust feature, Okta Verify, but by allowing outside device posture signals, Okta enables customers to experience a smoother IdP integration and fortified Zero Trust architecture, with deeper and more customizable posture checks. As of now, this feature is slated for early access in Q1 of 2024 and will be available for customers with Adaptive MFA.
Beyond Device Access
In the world of device access, Okta aims to improve user experience by creating a unified login experience for all a worker’s devices and apps. Tal Herman, VP of Product Management, describes Okta’s goal as “empowering the user without compromising security,” which they hope to accomplish with Desktop MFA and Desktop Password Sync.
With Desktop MFA, administrators will be able to enforce MFA on Windows devices (and soon macOS) when end users log into their managed devices. This not only includes a choice of possession factors (Yubikey!), but also allows end users to log in with or without internet access.
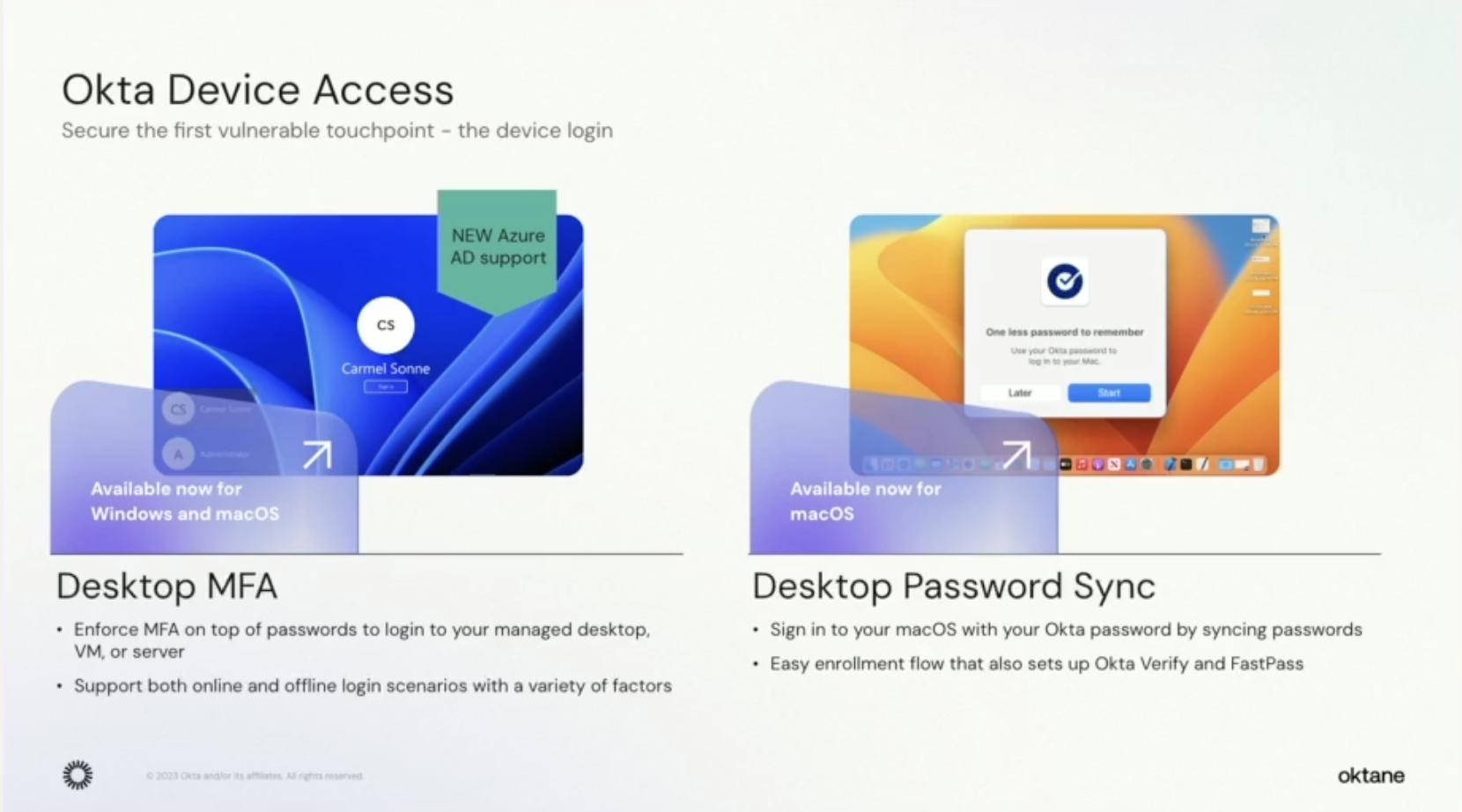
As for Desktop Password Sync, Okta looks to reduce the password burden by syncing end users’ local macOS account password with their Okta password.
Now, if you’re reading that line and tilting your head a bit, you’re not alone. On the surface it seems risky to eliminate one password and allow the other to be a skeleton key to two highly sensitive systems, but for administrators, it streamlines the Okta Fastpass enrollment experience as it enforces the passwordless, phishing-resistant authenticator at point of initial registration. This feature is currently available only to customers with (you guessed it) Okta Fastpass on Mac devices.
Beyond Identity Access Management
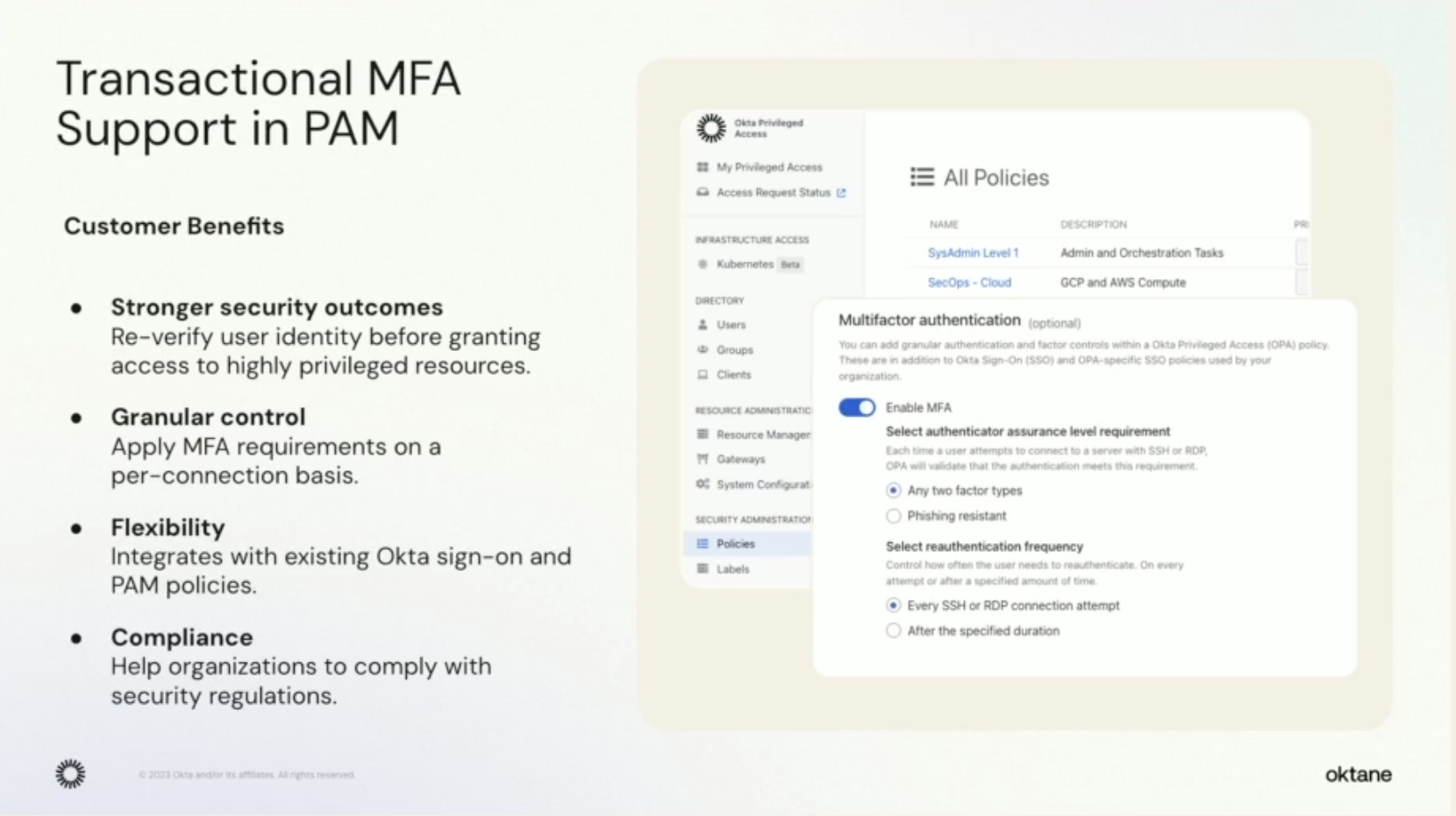
“Privileged Access Management (PAM) is here” proclaimed Arnab Bose, Chief Product Officer of Workforce Identity Cloud at Okta during the Go beyond MFA with Workforce Identity Cloud keynote. This announcement was immediately followed by boisterous applause, and PAM became one of the most talked-about features among Oktane attendees.
To explain the enthusiasm for a solution that restricts access to highly sensitive resources based on role, we’ll quote Okta’s own language about the problem it’s designed to solve: “A fragmented experience across identity, governance, and privileged access tools leads to a lack of policy enforcement.”
Okta Privileged Access promises to eliminate the silos that exist in workforce identity structures by unifying identity access, privileged access, and identity governance management systems. PAM will enable administrators to have full control of their Okta workflows and access from a single dashboard, where they will also see risk scores of user accounts and the access paths granted to those accounts.
This not only rids the headache of keeping track of access policies across systems, but allows for granular control of MFA at each level, in a way that’s easy to show auditors. Okta’s previously mentioned emphasis on user experience seems to be a real focus here, and they make a convincing case that a unified experience will drive adoption.
Starting in December 2023, PAM users will also be able to utilize the Secrets Vault. That’s an encrypted tool where organizations can store sensitive information such as passwords and OTP recovery codes based on a hierarchy of access rules within Okta–-making it different from most password managers as it focuses on maintaining least privilege across Security and IT teams.
PAM, currently available in limited early access, will also become generally available in December 2023 at a price tag of $14 per resource, which means it will be reserved for highly privileged teams.
Okta Previews New AI Tools
When companies bank on trends, that usually spells trouble for all involved; except Okta doesn’t believe AI is a fad, rather a tectonic shift in identity security. Shortly following a surprising acrobatic entrance, Okta CEO Todd McKinnon pronounced that “every company is an AI company.”
There is a compelling argument to be made that if the AI tides have risen, then security needs to follow; and that’s what Okta is doing with their new Okta AI product rollout.
Let’s take a look at what was announced across the Workforce Identity Cloud and Customer Identity Cloud keynotes (this is not an exhaustive list as we’ll be covering some later in the blog):
-
Guide with Okta AI
- Purpose: To provide developers with onboarding assistance and recommendations in their Okta authorization setup
- Expected: Q4 2024 (limited early access)
-
Identity Flow Optimizer with Okta AI
- Purpose: To provide developers on CIC in-line recommendations on the identity configurations and actions they should add to boost conversions and improve security in their apps
- Expected: Q4 2024 (limited early access)
-
- Purpose: A service offering from Okta personnel that will review your security posture and recommend improvements that will eventually become automated by Okta AI
- Expected: Currently available
-
Actions Navigator with Okta AI
- Purpose: To provide recommended actions that lessen friction and increase efficiency for developers in areas such as login through written prompts
- Expected: Q2 2024 (limited early access)
-
Policy Recommender with Okta AI
- Purpose: To provide administrators insights and policy recommendations based on security best practices and aggregated AI intelligence from the broader Okta community
- Expected: Q1 2024 (limited early access)
-
Governance Analyzer with Okta AI
- Purpose: To provide assessments regarding a user’s access risk based on past risk events while proactively launching access certification campaigns
- Expected: Q2 2024 (limited early access)
Like all AI-powered tools, these products don’t run on magic; they require vast amounts of customer data. And since the data Okta deals with is highly sensitive, there may be some discomfort among users with it being used to fuel policy recommendations. Okta seems to have anticipated this discomfort, and throughout these sessions, the mention of “billions of policies” was usually followed in quick succession by “anonymized customer insights.”
Identity Threat Protection
Identity Threat Protection (ITP) was another big hit among Oktane attendees. The phrase “game changer” could be heard in the crowd’s chatter and in subsequent conversations I had with peers. So let’s break down why.
The evolution of attack vectors such as session hijacking mean that breaches at point-of-authentication aren’t the only concern anymore; hackers can infiltrate a system at any time.
At its core, Identity Threat Protection (with Okta AI) looks to thwart bad actors, malware, and unrecognized access the moment it is detected during active sessions of Okta-protected apps. It’s made possible by a five-pronged process that weaves Okta’s proprietary AI throughout:
Shared Signals: utilizing the Shared Signals Framework (SSF), organizations will be able to link state changes and signals from their tech stack to their Okta instance
Continuous Assessment: during user sessions, Okta’s AI works in the background to assess any context changes in devices or sessions
Identity Threat Analytics: when risk levels or user context shifts, administrators are alerted and provided risk insights to assess the level of threat
Adaptive actions: depending on the severity of risk level/user context change, administrators can set up automated responses such an Universal Logout to neutralize the threat
Universal Logout: when a threat is detected, administrators have the ability to invalidate sessions and revoke a bad actor’s access immediately across “select leading apps,” a list Okta says it plans to expand
Okta also unveiled Log Investigator (with Okta AI), which can help both prevent breaches and learn from them if one has occurred. Eyed to be available Q3 of 2024, the new tool will help administrators analyze the data in their Okta system logs and prompt the AI (in plain English) for insights into risk scores, anomalies, and user access history.
Universal Logout—affectionately referred to as SSO (Single Sign Out) throughout Oktane—and ITP looks to become available to limited early access in Q1 2024.
Oktane 2023: AI’s Identity Coronation
As you let all of that paradigm-shifting-talk sink in and ponder its impact on your organization’s security, take a moment to reflect upon the words of Kelsey Nelson, Senior Director of Product Marketing at Okta. “[W]e have more data than ever before, but not necessarily knowledge.”
To me, that means that we may indeed need AI-powered security to battle AI-powered threats, but will still need human expertise and judgment to ensure that we use these tools in ways that reflect our values.
For more Oktane coverage and cybersecurity coverage at large, subscribe to the Kolidescope newsletter—you’ll get the latest issue as soon as you sign up!





